Analysing Network Attacks
Portfolio activities provided by Google Cybersecurity course 2024 | Completed by Emilio Mardones
View the Project on GitHub Ofendor/Portfolio2-Analysing-Network-Attacks
Analysing Network Attacks
Portfolio Activity 2 - TCP protocol & SYN Handshake log analysis with WiresharkIn this project, I used the information learned from known network attacks like DoS Attack, DDoS, SYN Flood Attacks, Ping of Death, and more. I also referenced material provided by:
- CISA: Understanding and Responding to Distributed Denial-of-Service Attacks (2024)
- NIST SP 800-61r3: Incident Response Recommendations and Considerations for Cybersecurity Risk Management 2024 (pages 21, 29, 33, 39)
Understanding how attacks impact networks from the target’s perspective helped me troubleshoot issues and respond in time, taking the right steps to mitigate damage and protect the network from future attacks.
All portfolio items represent fictional companies, IP addresses, websites, and emails, used strictly for educational purposes; and provided hands-on experience in real-world cybersecurity practices.
Activity Overview
In this scenario, working as a security analyst for a travel agency that advertises sales and promotions on the company’s website, I receive an automated alert from a monitoring system (Wireshark) indicating a problem with the web server. I attempt to visit the company’s website, but I get the message: “timeout error”. After using a packet sniffer to capture data packets in transit to and from the web server, I noticed a large number of TCP SYN requests coming from an unfamiliar IP address.

The web server appears to be overwhelmed by the volume of incoming traffic and is losing its ability to respond to the abnormally large number of SYN requests. This gave me a clear indication that the server is under attack by a malicious actor.
The next task was to quickly alert the managers about the problem by elaborating a report on the type of attack I discovered and how it was affecting the web server and employees.
Report
| Summary of the Problem |
|---|
| Today, we intercepted an alert from our traffic monitoring systems indicating a potential DoS attack.
We filtered some of the data logs provided by Wireshark and discovered the reasons why the systems weren’t responding smoothly.
After further investigation, the team concluded that the issues were linked to a foreign IP address that had been sending SYN packet requests, overwhelming our company’s network.
I attempted to visit the company’s website, but my request was denied with the message “timeout error”.
The team decided to take the server offline temporarily so the machine could recover and return to normal operating status.
We configured the company's firewall to block the IP address that was sending the attack.
We are aware that blocking this IP is a temporary solution, as the hacker could employ different techniques, such as spoofing other IP addresses, to initiate a new attack. Note: Network interception attacks work by intercepting network traffic and stealing valuable information, or interfering with transmissions, causing extensive damage to a company’s assets. |
| Website Function Explained |
|---|
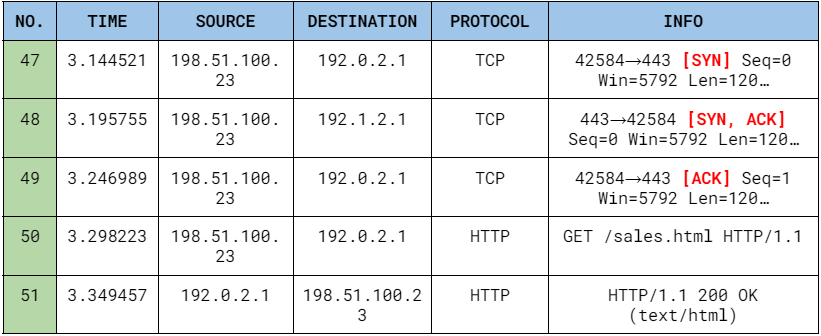
When the website visitors try to establish a connection with the web server, there is a three-way handshake that occurs using the TCP Protocol.
The TCP Protocol is part of the Transport Layer in the TCP/IP Model and is in charge of all internet communications that allow two devices to form a connection and stream data. This protocol ensures that the data is reliable and is transmitted to the destination service without any issues using the ‘Handshake’ process. This ‘Handshake’ consists of the following steps:
|
A normal transaction between a website visitor and the web server would be like:
Network Traffic Log
| The Attack Explained |
|---|
|
According to CISA, a DoS Attack involves a single source used to overwhelm the target system with a flood of traffic or resource-consuming requests.
The malicious actor typically uses one computer or a small network to generate the attack. The goal is to render the target system unavailable to its intended users and deny access to resources or services. A malicious actor can take advantage of the TCP protocol by flooding a server with SYN requests for the first part of the handshake, as shown in the Wireshark captures. If the number of SYN packets is greater than the server resources available to handle them, the server will become overwhelmed and unable to respond. This is a Protocol-Based Attack, also known as a SYN Flooding Attack, that exploits vulnerabilities in the network protocols to disrupt their targets. These types of attacks normally target the bandwidth of the Network Layer from the TCP/IP Domain and the Transport Layer in the OSI Model. The interactions with the attacker’s IP address 203.0.113.0 are shown in red in the Wireshark graphic. Initially, the SYN requests are answered normally by the web server (log items 52-54). However, the attacker continues sending SYN requests, creating an abnormal environment for the network. The green colored log entries show the responses to normal visitor traffic, which means that until this point the server is still capable of managing its bandwidth and providing access to the network for the source IP address 198.51.100.14 (check log items 55, 56, 58, 60, 62 in the graphic). In the next rows, the log begins to show the struggles the web service is having to keep up with the number of SYN requests coming in at a rapid pace, generating the following log errors:
|


Steps to Follow
In the event of an issue of this magnitude, there are a series of steps that the organisation should take both during and before the attack to demonstrate its resilience.
During a DoS attack, we have to focus on how to respond. According to NIST and their Incident Response Recommendations and Considerations for Cybersecurity Risk Management, the main steps to consider are:
- Identify the Attack as soon as possible: Observe the behaviour of the network and alert the abnormalities shown by traffic analysers to confirm the attack.
- Activate Incident Response Plan if any: The organisation’s plan will outline the roles and responsibilities of key personnel and communications during the event of an attack.
- Gather Evidence: Collecting and documenting as much information as possible about the attack will provide useful evidence for reporting the incident to law enforcement or future analysis.
- Implement Traffic Filtering: Configure the network structure, firewalls, or IDS to filter out malicious traffic.
- Communication: Communication internally and externally is essential to maintain a clear report to key stakeholders, including employees, customers, vendors, etc.
- Learn from the Attack: After the situation is resolved, conduct a deep post-incident analysis to understand the attack vectors, patch the affected systems, expose the current vulnerabilities, and learn our lessons. With this information, update whatever is necessary, patch the respective systems to prevent future attacks and strengthen the company’s cybersecurity mindset.
Since the organisation can’t predict when a DoS attack will occur, it is imperative that our network defenders implement best practices to minimise the potential damage of these types of attacks:
- Risk Assessment: A proactive approach for risk assessments to determine the vulnerabilities of the organisation and identify the weak points and the potential impact a cyber attack can provoke.
- Network Monitoring and Traffic Analysis: Tools and Intrusion Detection Systems to identify any abnormality or suspicious traffic patterns.
- Captcha: Integrating captchas into a website or online service will help differentiate between human users and automated bots.
- Incident Response Plan: A comprehensive plan to outline steps to be taken in the event of a DoS attack will ensure effective mitigation of the problem using the correct strategies.
- Firewall Configuration: To filter out suspicious traffic patterns and block traffic from unknown IP addresses. Also, consider implementing rate limitations to prevent overwhelming traffic.
- Patch and Update Systems
- Employee Awareness and Training: Educating employees about DoS attacks is beneficial for the company, as it helps maintain service availability during an attack.
- Backup and Recovery: Regular backups are critical in case of a disaster recovery plan to recover quickly after an attack and minimise potential data loss.
Key Takeaways
In response to today's DoS attack, our network analyzers (Wireshark) identified traffic anomalies linked to an unknown IP address, causing customer service disruptions. As a result, a SYN flood attack overwhelmed the company’s network. The temporary solution of configuring the Firewall to block the IP address allowed the server to recover, but it is critical that we implement immediate and robust defensive measures to prevent future incidents.
Moving forward, strategies such as proper firewall configuration, employee training, regular backups, and a comprehensive incident response plan are critical to safeguarding information and ensuring availability against future attacks.
We recommend conducting a post-incident analysis to patch vulnerabilities and strengthen resilience against TCP protocol exploitation and other similar cyber threats.